
 No matter how good your technical defense and security policies are, cyber criminals can easily come up with new phishing techniques to reach their targets
No matter how good your technical defense and security policies are, cyber criminals can easily come up with new phishing techniques to reach their targets
Every cyber security expert agrees that most cyber attacks are successful due to “human error”. Another fact that they all agree on is that the majority of cyber attacks are launched through emails in the form of phishing.
According to an article from Security Boulevard, 91% of cyber attacks start with an email. Another article states, 85% of all organizations have been hit by a phishing attack at least once.
Addressing at the RSA Conference 2016 Abu Dhabi, Steven Malone, a cyber security expert, said “Historically businesses have turned to advanced technology to protect themselves from cyber attacks, but this approach is just not enough. With more than 90% of cyber attacks using email as the attack vector, it is essential that organizations strengthen their email security strategy as well as create a ‘human firewall’ because hacking a human is often easier than breaching a business.”
So, how do we eliminate phishing attacks? Well, we can’t. However, what we can do is learn to detect the trap before we fall into it. This can be a challenging task since cyber criminals constantly come up with new, sophisticated phishing techniques to trick their targets. The first step towards avoiding phishing attacks is to be aware of how these different techniques work.
Table of Content
5 Types of Phishing Techniques
Email Phishing
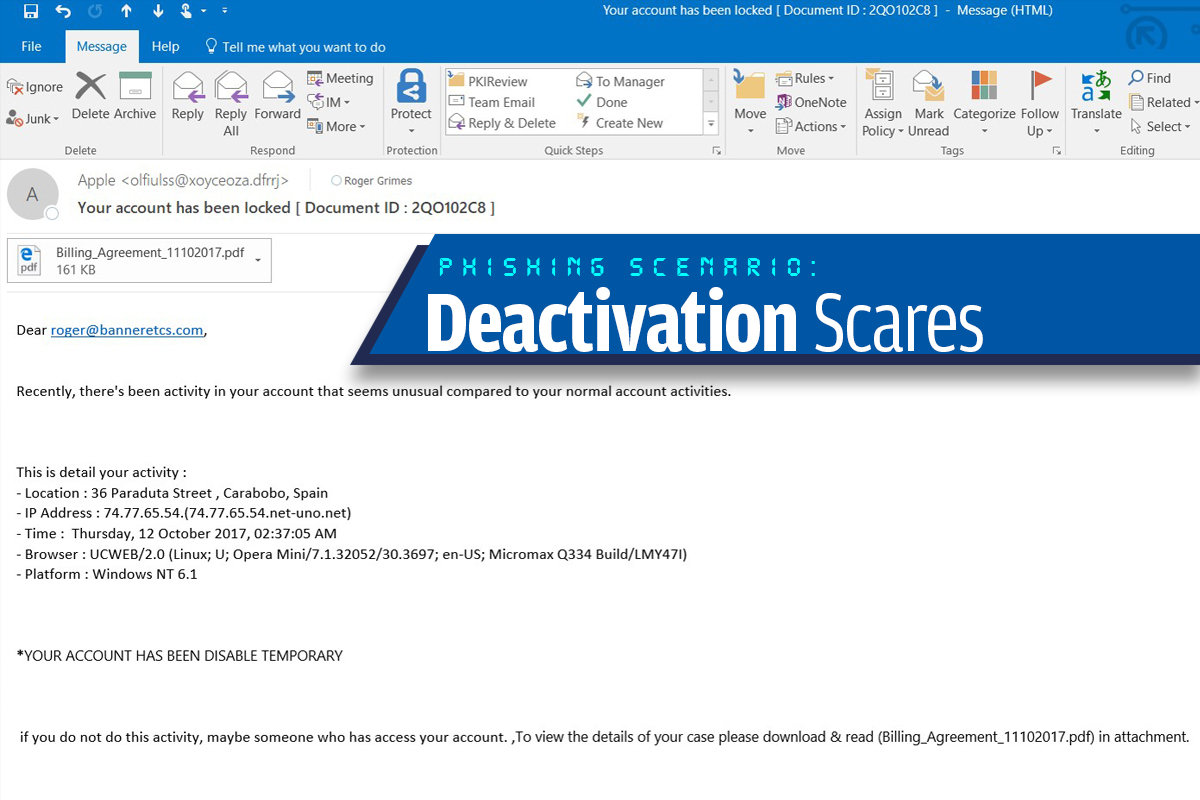
Email phishing is one of the most common phishing techniques and has been widely used since the 90s. In an email phishing campaign, cyber criminals obtain a number of email addresses and send out numerous emails looking for someone to fall into the trap. In order to successfully run this campaign, cyber criminals mostly use common tactics like inducing panic, creating a sense of urgency, or offering something the victim can’t resist.
Email Phishing Attack Example
Smishing
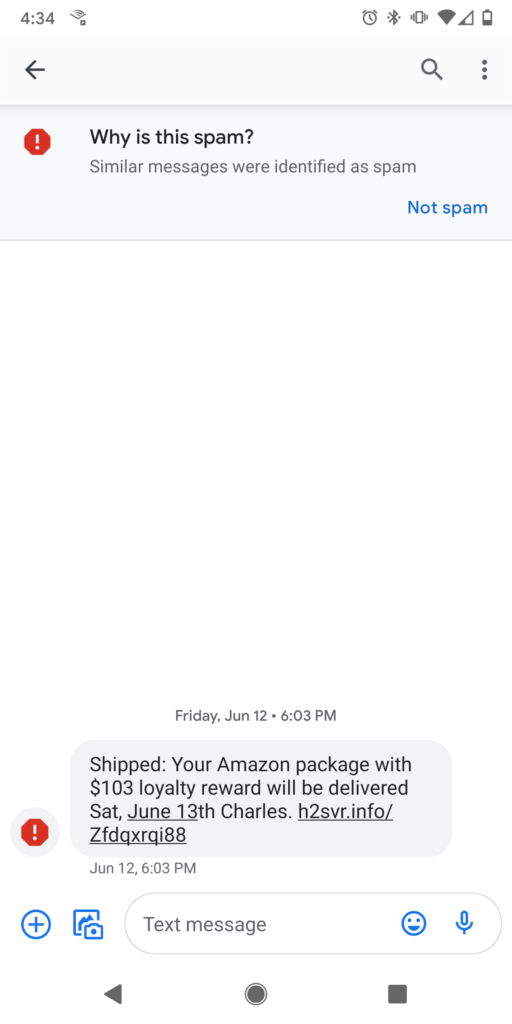
It is similar to email phishing. However, criminals use text messages or SMS (Short Message Service) instead of emails. In the majority of smishing campaigns, cyber criminals impersonate a bank or other trusted organizations to send out messages embedded with malicious attachments. The embedded links often redirect the victims to a fake website, prompting them to give up personal or confidential information.
Smishing Attack Example
Vishing
Just like smishing and email phishing, vishing is used by cyber criminals to gain your sensitive information. However, these attacks are carried out through voice calls. Cyber criminals call their victims to gather their personal information. They can use the gathered information to compromise your personal accounts, gain access to your bank accounts, or commit identity theft.
Search Engine Phishing
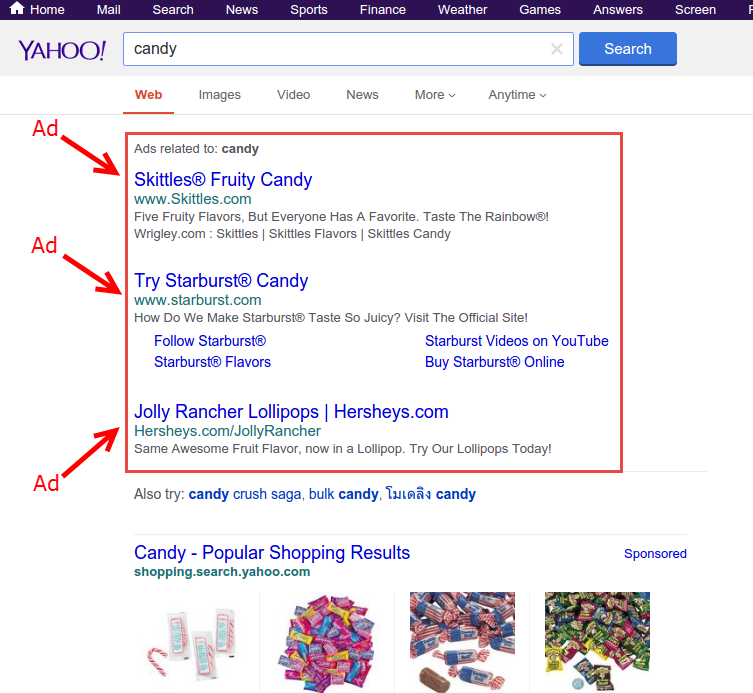
In search engine phishing, cyber criminals build a phishing website. These sites are indexed by legitimate search engines and offer lucrative deals or really cheap products. These websites are carefully designed to catch your attention. They are really hard to differentiate from legitimate websites, making it easy for the victims to fall into the trap.
Search Engine Phishing Attack Example
Whaling Phishing
Just as the name suggests, cyber criminals go for the ‘BIG FISH’ in whaling attacks. Similar to spear phishing, threat actors go after specific targets, which are often C-suite executives like CEO, CFO, COO, etc.
In a whaling attack, cyber criminals often impersonate a legitimate authority to trick the C-level executives into clicking on a malicious link that either redirects them to phishing websites or enables malware to get automatically downloaded in their systems. These websites are designed to collect their personal information.
How to Avoid Various Phishing Techniques?
Now that you know how these phishing techniques work, you might want to know how to avoid them, right?
The best solution to avoid phishing attacks is to stay vigilant and well-informed about the prevalent and emerging phishing techniques. There are many phishing awareness training tools available in the market that can help you train your employees in the basics of cyber security. One such tool is ThreatCop. This tool helps in simulating phishing attacks to provide employees with real-world experience in dealing with a phishing attack. There are numerous benefits of simulated phishing training for an organization, such as:
- Increasing the awareness level of the employees
- Making employees vigilant enough to detect cyber attack attempts
- Arming employees with the knowledge needed to combat cyber threats
- Promoting cyber hygiene in the workplace
- Boosting cyber resilience of the workforce
- Improving the cyber security posture of the organization
So, what are your thoughts on different phishing techniques and the ways to avoid them?
Turn Your Employees Into A Cyber Threat Shield
Make your employees proactive against prevailing cyber attacks with ThreatCop!

