You must be receiving official emails from your service providers very often. While you find those emails annoying, hackers find them as an opportunity. They use this opportunity for clone phishing.
Clone phishing is a type of phishing attack where the hacker copies a legitimate email message that is sent from a trusted organization. The hacker alters the email by replacing or adding a link that redirects to a malicious and fake website.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Further, the email is sent out to a large number of email receivers and the hacker watches out for the victims who click it. When a victim successfully falls for the cloned email, the hacker forwards the same forged email to the contacts from the victim’s inbox.
As mentioned in one of our blogs “How to Spot the Most Common Types of Social Engineering Attacks?” Google has registered 2,145,013 phishing sites as of January 17, 2021.
Clone phishing is a next-level attempt of tricking the recipient’s suspicions beyond spear phishing. This attack has got the following characteristics:
- A spoofed email address will appear to have come from a legitimate source
- The attached file or link in the email is replaced with a malicious version
- The cloned email will claim to be a revert of the original email or an updated version of the original email
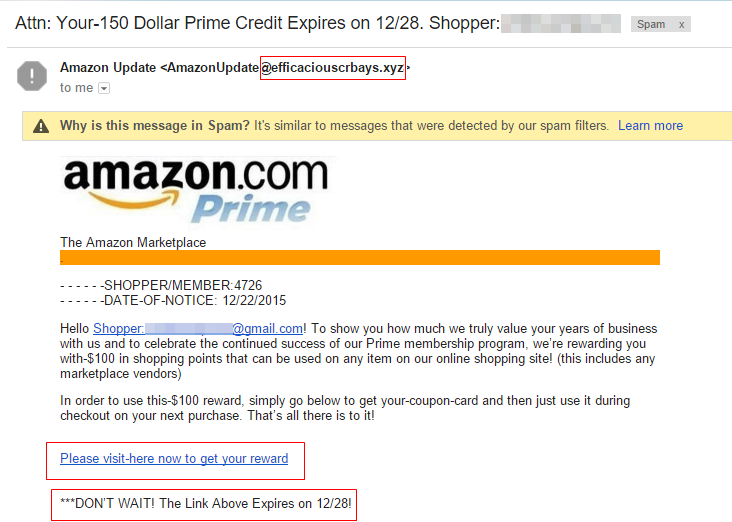
Users assume that the websites or domains they interact with are safe. But in reality, hackers trick users by impersonating domains and cloning websites. This is why the clone phishing attack is considered the most harmful one because it is hard for victims to suspect a spoofed email.
How to Prevent Clone Phishing?
To remain safe from online scams and prevent phishing attacks, it is important to stay secure by implementing some security measures. The following cybersecurity tips can help you in securing your organization from cyber frauds:
- Always check the sender’s email message
- Before clicking on any landing page, hover over the link in the email to ensure its authenticity first
- Make sure to follow up with the organization that has sent the email
- Keep your credentials secure by not sharing them with anyone in particular
- Look out for suspicious errors in the email as cloned emails are not 100% legitimate in looks
- Always submit your information to websites that have an “HTTPS” prefix before the URL of the website
- Secure your organization by educating your employees with security awareness training
An organization can only be fully protected if its employees are well aware of harmful cyber attacks. They should be less vulnerable and more proactive enough to combat emerging cyber attacks.
With a vision to enhance cyber defense capabilities within employees, companies like Threatcop offer a wide range of cybersecurity solutions from security awareness training and email security solutions (TDMARC and TPIR) for organizations. This leading cybersecurity firm provides a huge range of security tools and services to ensure that organizations are secured against prevailing cyber risks.
Strengthen the Weakest link in Your Organization
Employees are the weakest link in the cybersecurity chain of the organization. They should be primarily trained in cyber awareness in order to reduce the existing cyber risks within the organization. Threatcop’s security awareness tool, TSAT is designed and developed for this purpose. The tool helps in turning employees into the strongest link in the organization’s cybersecurity chain.
TSAT is a cyber attack simulator and security awareness tool that assess the real-time security threat posture of the organization. This tool assesses the level of vulnerability of employees and trains them on the basis of the Employee Vulnerability Score. It comes with a 2000+ cybersecurity awareness content library which includes newsletters, videos, a gamified quiz, and much more!
