

Today, the ever-evolving technology has taken society to the next level of evolution. However, it has also paved a path for malicious actors to misuse it and exploit unwary users. Day after day, cyber criminals are growing more sophisticated and smart. They have been honing their skills in order to bypass the latest security standards and obtain money and data illegally.
Phishing and pharming are two major types of cyber attacks that involve tricking others into providing their personal information. Although cyber criminals use both these tactics to obtain sensitive information, they work differently.
Table of Content
What is Phishing?
Phishing is basically a social engineering attack that uses emails as a disguised weapon. In short, the cyber criminals impersonate a legitimate source to trick the target into clicking on a malicious link or attachment to acquire their personal information.
The scary part is, cyber criminals are not only limited to using emails for launching phishing attacks. They can also phish over a website and sometimes go with SMS (smishing) or voice call/messages (vishing) to trick users. According to a report from Security Boulevard, 97% of the users are unable to recognize a sophisticated phishing email.
In another report from The National News, 94% of UAE businesses experienced phishing attacks in a year. The same report also highlighted that 77% of email spoofing attack victims had money and valuable data stolen in the UAE, as compared to the global average of 73%.
Example of a Common Phishing Scam Attempt
- A spoofed email impersonating incometaxindiaefilling.org.in to distribute it to as many taxpayers as possible.
- The email claims that the taxpayers are qualified to obtain a refund and prompts them to submit the tax refund request within 3 days.
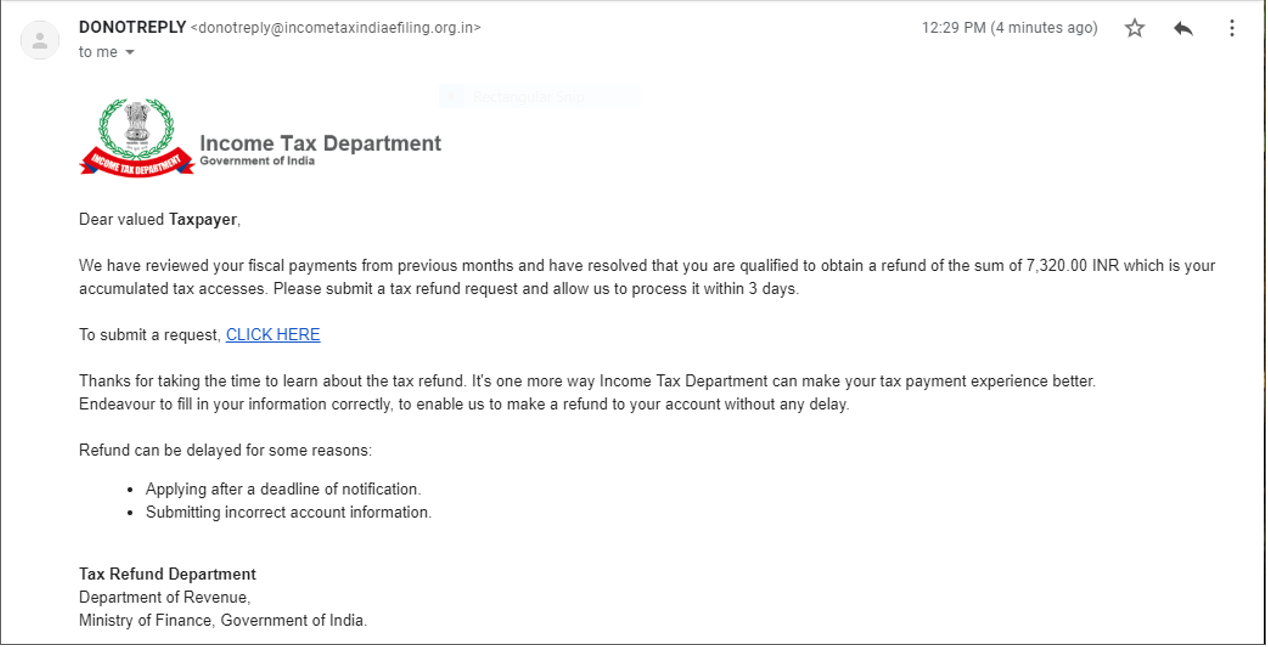
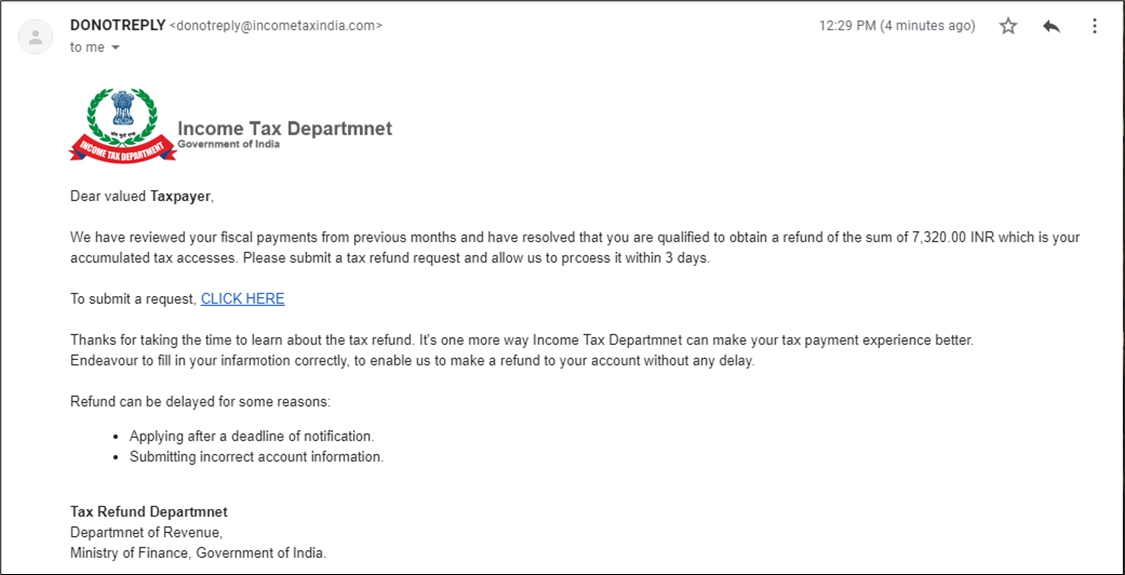
Several things can happen if the users click on the link to submit the request. The users might be redirected to a bogus page, where they may be asked to submit their personal information.
The hackers can harness the information and use it for other malicious activities such as identity theft. This can often lead to more disastrous and grievous consequences. Furthermore, on clicking on the link, the users might end up downloading malware infections like ransomware.
What is Pharming?
Pharming is the combination of two words “phishing” and “farming”. Pharming refers to the redirection of the users to a fraudulent website without their consent.
For example, an employee routinely logging into a payroll account may be redirected to a forged website instead. And, if the fraudulent website looks legitimate enough, the victim may end up getting tricked.
The motive behind phishing and pharming attacks remains the same, however, the techniques used to carry out these attacks are different. In pharming, cyber criminals carry out a two-step procedure in order to succeed.
First, the malicious actors push a malicious code on the victim’s computer or server. Second, the code redirects the victim to a fraudulent website where they are asked to enter their personal information.
To completely understand how pharming works, one must understand how Domain Name System (DNS) servers work. Whenever a user enters a domain name, the DNS servers translate that domain name into an IP address. It is the IP address that indicates the actual location of the website.
So, once a user visits a certain website, a DNS cache forms to prevent the need for visiting the server each time the user returns to that site. However, cyber criminals can corrupt both the DNS cache and the DNS servers through pharming. As a result, the users assume the bogus website to be legitimate and end up submitting their personal information.
How to Prevent Phishing and Pharming?
Several enterprises are implementing security protocols and taking steps to protect customers from phishers and pharmers. For example, in April 2020, the UAE Banks Federation launched a fraud awareness campaign to prevent digital banking service users from falling for scams. However, all it takes is one click for someone to fall for a scam.
Though as harmful as these attacks are and as easy as it is to fall for these attacks, they can be easily prevented. Taking the basic precautions listed below can help you and your organization in mitigating the risk of these kinds of attacks:
- Look Out for URLs
Make sure your employees pay attention to the URL of the website when browsing on the internet. Legitimate websites always have the upper domain or TLDs (Top Level Domains) such as .org, .com, .edu, .net, etc. For example, www.google.com.
However, if on visiting the site, it is www.google.ad.com or www.Goodle.com – even a minor mistake in the website URL is a hint that the DNS cache has been compromised.
- Brand Monitoring
As an organization, promoting your brand is essential to foster the identity of your company. If cyber criminals impersonate your brand for malicious purposes, it can bring down everything you have worked for. Therefore, it is highly recommended to keep track of how your brand is being represented online.
- Avoid Clicking on Links
Make sure that your employees pay extra attention whenever they click on a link embedded in an email, especially one from an unknown source. It is advisable to make a habit of hovering over the link to check its destination before clicking on it.
Additionally, implement a phishing incident response tool like TAB to enable the employees to report any malicious links or attachments getting delivered through an email.
Cyber Security Awareness Program
Even if your organization has implemented all the best cyber security tools, it all comes down to how cyber aware and vigilant its employees are. So, organizations should conduct regular cyber security awareness training programs to raise awareness amongst the employees.
Educating employees by using cyber security awareness training tools like ThreatCop can help in preparing them to face existing and emerging cyber threats.
ThreatCop comes with fully customizable campaign templates that can be designed based on the employees’ weaknesses or the organization’s environment.
For instance, an employee working in the accounts department is more likely to open an email or click on the link embedded in it if it is related to the organization’s financial statements. Simulating phishing attacks on the employees can help them understand how to spot phishing attempts and react to them in real life.
No matter how strong an organization’s IT security infrastructure is, addressing the employees is a must for every organization. Remember, all it takes is one simple click for an employee to jeopardize the whole organization.
Turn Your Employees Into A Cyber Threat Shield
Make your employees proactive against prevailing cyber attacks with ThreatCop!

