Email is the most useful business communication channel for organizations. But the biggest challenge is that it is one of the most common mediums for hackers to attack businesses. Email threats are the primary cause of cyber attacks globally.
There are different kinds of cyber threats looming on the horizon, and among them, email-based attacks are the most common and severe. Typically, in email-based attacks, attackers craft fraudulent emails using forged sender’s addresses to lure victims into transferring money or giving out their personal information, credentials, or other sensitive data.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What are Email Threats?
Email threats are one of the biggest risks faced by organizations in today’s cyber threat landscape. Cybercriminals continuously exploit the services and vulnerabilities of emails and target organizations. Some of the common threats to emails are phishing, spoofing, business email compromise, etc.
According to Digital in the Round, 3.4 billion phishing emails are sent on a daily basis.
Email threats are the leading cause of cyber attacks and are responsible for the majority of the financial damage done to organizations worldwide. They not only disrupt the cybersecurity framework of a company but also obstruct its everyday operational activities.
Read more about Email Security
What are the Types of Email Threats?
Since the pandemic, the world has witnessed a rising rate of digitization and a rapid increase in the ‘work from home’ culture. This has considerably threatened the cybersecurity landscape. The majority of the email-based attacks are carried out through phishing scams. However, ransomware and business email compromise scams have also resulted in significant financial and reputational losses for organizations.
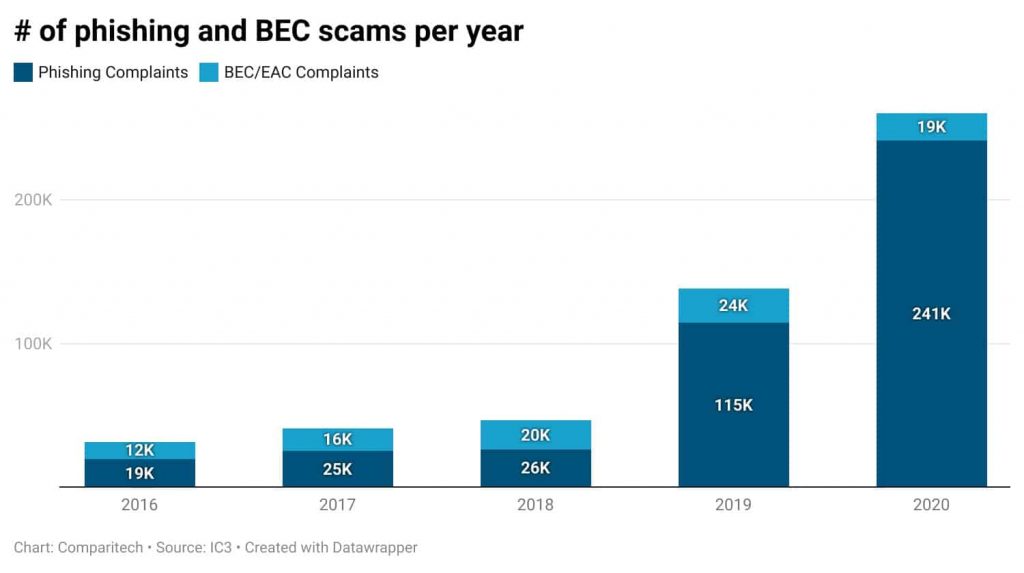
Phishing Scam
In recent years, the number of phishing attacks has increased tremendously. Along with that, the sophistication of these attacks has also grown. Cybercriminals are using new tactics to lure users into phishing scams.
96% of phishing scams are carried out through emails. (Source: Cincinnati Ball)
There are multiple negative impacts of phishing emails, such as loss of money, damage to reputation, loss of intellectual property, and, mainly, disruption of operational activities.
Read more about Phishing and Pharming
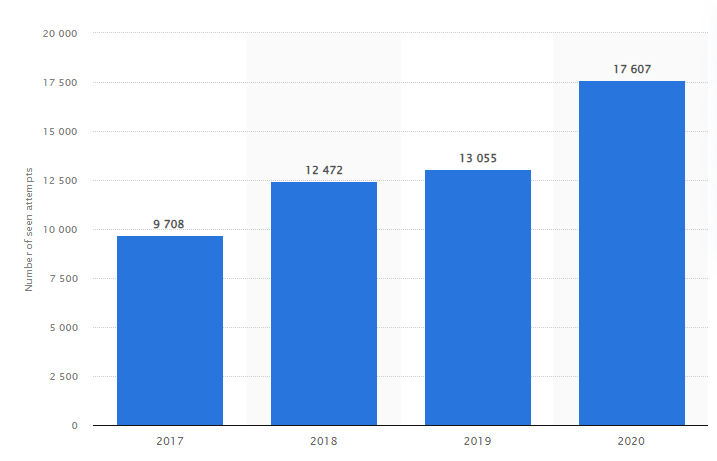
Ransomware Attacks
While phishing attacks are more common and frequent, ransomware attacks are the most financially damaging. In many cases, to launch ransomware attacks, threat actors implant malware in a software or file and then attach it to spoofed mail. This malware infects the system, giving access to cybercriminals and blocking the use of the systems for users.
According to AFCEA, the average ransom has increased from $5,000 in 2018 to $200,000 in 2020 during ransomware attacks.
The major impact of ransomware attacks is loss of productivity, along with an increase in the requirement for resources to resolve the issue. It has been reported that on average, it takes 60 days to resolve a ransomware attack. That’s why organizations employ a policy of threat hunting to ensure the prevention of ransomware attacks.
Read more about Ransomware Detection through Threat Hunting
Business Email Compromise Attacks
A BEC attack is commonly also known as CEO fraud. This is because it is carried out through the impersonation of C-suite employees. In these attacks, threat actors often impersonate any senior-level employee to carry out scams on junior employees, asking them to make financial transactions or share private data.
According to HelpNet Security, 34% of the respondents of a survey stated that finance-related employees have been the targets of spear phishing or business email compromise attacks.
A BEC attack has a significant impact not only financially but also causes immense damage to the reputation of the company. BEC attacks are continuing to be the biggest email threats to organizations.
Spyware Email Threats
Spyware is another type of cyber threat that can be carried out through emails, giving rise to several security and privacy issues. In these cases, cybercriminals inject spyware software into the victim’s system through email. This spyware is downloaded either through an attachment or by clicking on a link given in the mail. Spyware allows the attacker to monitor all the activities of the target.
Malware Email Threats
Malware is software or attack script used to infect a victim’s system to conduct data breaches or credential theft. Ransomware attacks are based on malware attacks as they infect the system with malware-infected software. The impact of attacks led by malware is quite huge and it disrupts the entire cybersecurity infrastructure of the victim organization.
How to Prevent Email-Based Attacks?
There is a set of best practices that can be followed by employees and people, in general, to prevent email-based threats. Some of these practices are listed below.
Strong Passwords
Passwords are the first line of defense for protecting email accounts. Every organization needs to incorporate a strict policy to make sure that every employee is using email passwords according to set standards.
Read more about How to Keep Your Password Safe From Hackers?
Two-factor Authentication
Every email account is protected with a password. Two-factor authentication is to implement another layer of security to protect your email account in addition to your password. When 2FA is implemented, the user gets a notification of a compromised login attempt in case a threat actor tries to break into the account.
Phishing Incident Response Tool
Organizations should employ a tool that allows the reporting of phishing emails. While email service providers already provide a filter to identify phishing emails and sort them into spam, the rising level of sophistication of cyber attacks enables much phishing and spoofed emails to still land in inboxes. A phishing incident response tool is meant to empower employees to detect and report suspicious emails.
Know more about the Threatcop Phishing Incident Response Tool
Educate Employees
According to IBM, 95% of cyber attacks and cybersecurity breaches are caused by human error.
Human error and employee unawareness are the leading causes of major email-based attacks. That’s why it’s extremely important to educate employees. Employee cybersecurity awareness training should be an essential part of an organization’s cybersecurity framework.
Read more about Employee Cybersecurity Awareness Training
Standard Email Authentication Protocols
One of the most prominent mechanisms to prevent email-based attacks is by securing the email domain against spoofing. This is done by using the three standard email authentication protocols such as DMARC, SPF, and DKIM.
Read more about SPF: An Email Authentication Protocol
Read more about DKIM: An Email Security Protocol
Read more about What Is DMARC And How Does It Work?
Email Threat Protection
Email security is the key to email-based threat protection. There are key elements to email security, such as securing an email domain or conducting employee security awareness, that safeguard the email platform from cyber attacks. Email threat protection is done by using several tools and services that are meant to secure the email domain as well as the employees.
The objective of threat protection is to empower the cybersecurity framework of the organization to defend against cyber attacks. Nowadays, organizations are looking for security solutions that are based on artificial intelligence and machine learning, such as secure email gateways.
Email Security: Every Organization’s Goal
Email security involves a comprehensive set of activities that incorporate tools and services meant to protect email accounts as well as email domains. There are various solutions on a technical level, such as email authentication protocols, secure email gateways, etc.
Organizations need to implement the above-stated technologies to secure email domains. In addition to that, they need to empower the employees by employing phishing incident tools such as Threatcop Phishing Incident Response Tool (TPIR) and security awareness training. This will train the employees to become better at defending the organization and themselves against email threats.

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
