

Not even half the year has passed; cyber-attacks have already terrorized the world. However, attack vectors like Phishing and Ransomware have caused the maximum loss to organizations across the globe, collectively. Within the period of two years, these attacks have seen a 97% increase. Ransomware attacks alone have cost more than $75 billion last year.
With ransomwares like ‘Dharma’ making a comeback, we present you the top ransomware attacks that have aggressively affected various organizations within the first half of this year.
Cerber
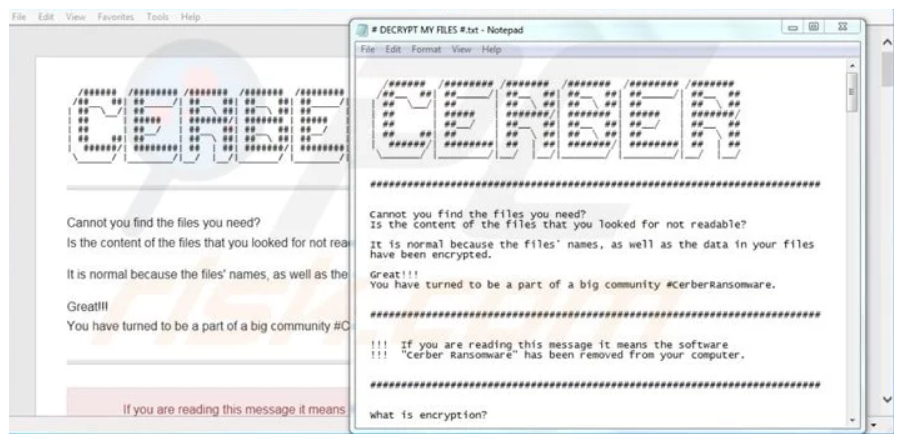
This ransomware uses an elaborate phishing campaign service that targets cloud-based Office 365 users. Victims receive an email with infected Microsoft Office document as an attachment. Once opened, the ransomware runs silently in the background during the encryption phase and does not provide any indication of infection to the user. Once the encryption is completed, users will find ransom notes in encrypted folders and often as a desktop background.
Cerber has affected millions of users globally, except in Post-Soviet countries. Cerber uses strong RSA encryption and currently, there are no free decryptors available for this ransomware.
Bad Rabbit
Organizations present mainly in Eastern Europe and Russia have been attacked by the Bad Rabbit ransomware attack. The ransomware is disguised as Adobe Flash installer and spreads through ‘drive-by download’ on the compromised websites. The Flash download is installed in websites using JavaScript that is injected into the Java files or HTML of the affected websites. Once the person clicks on the malicious installer, his/her computer gets locked. The entire process compromised the system of thousands of people.
Dharma
Dharma is a form of cryptovirus that uses contact email as well as random combinations of letters to mark encrypted files. The ransomware was first released in 2016 and is regularly updated. Dharma uses an AES 256 algorithm for encrypting files while it simultaneously deletes shadow copies. The latest variants of 2019 includes file extensions .gif, .AUF, .USA, .xwx, .best, and .heets.
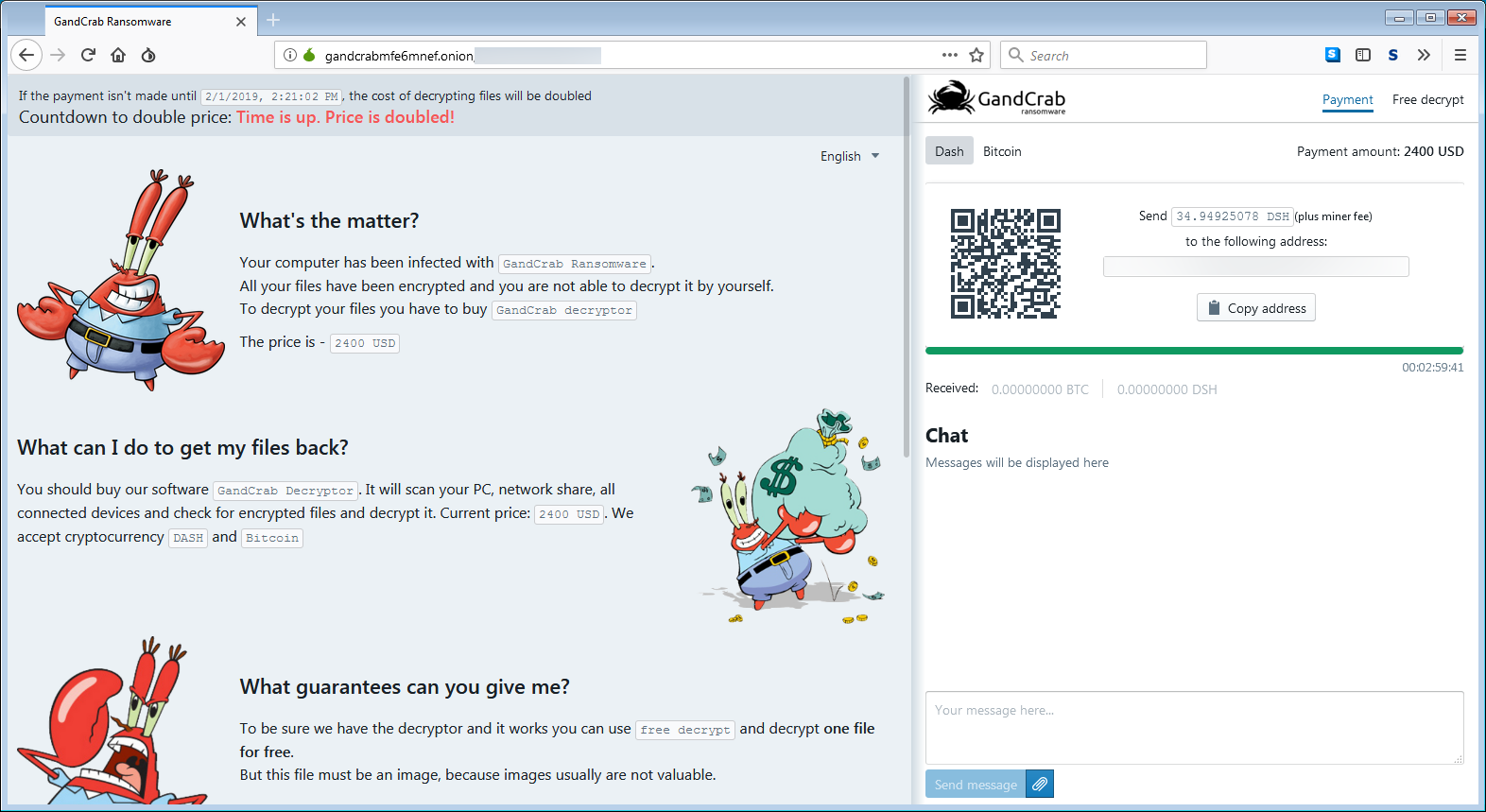
GandCrab
The GandCrab ransomware was one of the most popular ransomwares of the year 2018. At the end of January 2019, it had already infected more than 48,000 nodes. It depends on Microsoft Office macros, VBScript and PowerShell in order to evade detection. GandCrab uses ransomware-as-a-service (RaaS) model for maximizing delivery while focusing on consumer phishing emails.
Jigsaw
The Jigsaw ransomware not only encrypts user’s files but also, deletes them. Victims have only 24 hours to pay 150 USD as ransom. If the victim fails to meet the deadline, the ransomware starts deleting files every hour and increases the number of files for deletion every time.
Katyusha
First observed in October 2018, Katyusha is an encryption ransomware that encrypts files by adding extension “. katyusha” and demands 0.5 BTC as ransom within the period of three days. If the ransom is not paid, attackers publically release the data. The malware package contains DoublePulsar and EternalBlue exploits which are used to spread over the network. It also deletes shadow copies from the system. The ransomware is delivered to victims via malicious email attachments.
LockerGoga
LockerGoga is one of the most destructive types of ransomware that has hit many industrial and manufacturing firms thus, causing significant harm. It forcibly logs off victims from the infected device. It has a very different approach since the victims are not able to see the ransom message and the instructions on how to recover files. After hitting the French engineering consulting firm Altran, it has also hit Norsk Hydro as well as two other major US-based chemical companies.
Ryuk
Ryuk specializes in targeted attacks and has produced more than $3.7 million in bitcoin that is spread across 52 payments. The malware uses robust military algorithms like ‘RSA4096’ and ‘AES-256’ for encrypting files and it demanded ransoms ranging from 15 to 50 bitcoins.
What could have been done in this situation?
- The best way to prevent a ransomware attack is by following healthy security practices including keeping offline backups and not clicking on suspicious attachments in order to avoid the infection.
- Limit privilege for administrative access unless it is absolutely needed and those who require the administrator accounts should only access the account when it is necessary.
- Implement Software Restriction Policies (SRP) in order to prevent the execution of programs from common ransomware locations including temporary folders, compression/decompression programs or supporting popular Internet browsers.
- The most important security measure is to keep your employees educated. Employees should undergo a cyber security awareness and training for being prepared to fight back cyber attacks. This training should be backed up with regular assessment of employees’ knowledge. It could be achieved with tools like ThreatCop that help in building cyber resilience among employees which serves as a people-risk assessment engine to protect the organization.

