
“Ransomware is not only about weaponizing encryption, it’s more about bridging the fractures in the mind with a weaponized message that demands a response from the victim.”
― James Scott, Senior Fellow, Institute for Critical Infrastructure Technology
As the recent ransomware attacks on Birmingham College and computer giant Acer have undeniably proved, cyber criminals are putting their best foot forward when it comes to robbing organizations. Cyber criminals are constantly working to come up with new techniques to launch ransomware attacks and earn huge paychecks in return.
In one of our previous blogs “40% Increase in Ransomware Attacks in Q3 2020”, we mentioned how ransomware attacks are growing in volume and frequency. Since then the number of these attacks has only been increasing. In fact, ransomware has risen by 62% since 2019 according to a report from Security Magazine.
So, it is time now for the cyber security experts to accept the fact that ransomware is not going anywhere anytime soon! Consequently, they will need to come up with a solution to combat the attack vector that hampers organizations’ growth so thoroughly. Is this task difficult? Yes. But is it impossible? No. Cyber criminals work hard to access our systems, so we need to work smart to prevent them from succeeding!
Before we dive into the ‘smart moves’, let’s find out what actually happened with Birmingham College and Acer.
Table of Content
Birmingham College Hack
According to the report, Birmingham college was forced to ask all of its 20,000 students to stay at home for a week after they were hit by a ransomware attack. It had not even been two weeks since they had returned to the college following an extended lockdown due to the Coronavirus pandemic.
“Ransomware attacks on schools, colleges, and universities are estimated to have doubled globally over the past year because the switch to remote learning has stretched their IT resources, and criminals believe this makes them a soft target. The UK’s National Cyber Security Centre warned of this sharp increase in September 2020.” – Jon Niccolls, EMEA & APAC Incident Response Lead.
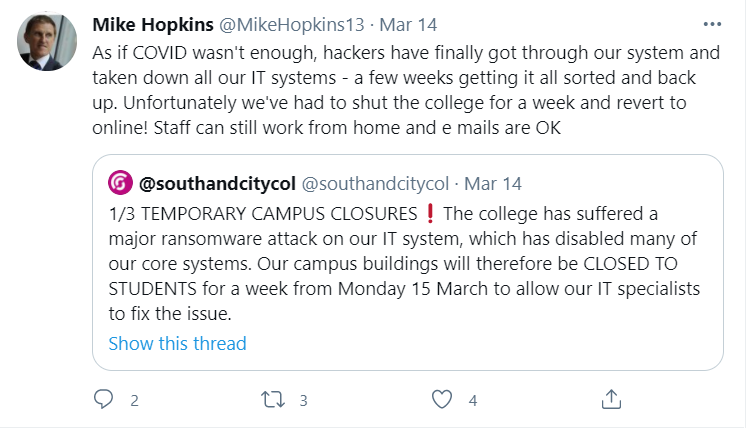
The source behind the attack has not been identified yet. The students were informed about the attack in a series of tweets, which also stated that the classes will be reverting to online teaching while the experts attempt to recover the systems.
$50 Million Ransomware Attack on Acer
In another cyber incident, computer giant Acer was targeted by a ransomware attack. According to an article by Bleeping Computer, a group of cyber criminals known as REvil is believed to be responsible for the attack.
It is believed that the hackers gained access to Acer’s network through a Microsoft Exchange vulnerability. Then the attackers demanded $50,000,000, which is the largest known ransom to date. The same group of hackers is also associated with last year’s ransomware attack on Travelex, a London-based foreign exchange company.
The article also added that the attackers announced the breach on their data leak site and shared some images of the stolen data as proof.
As of now, Acer has not confirmed the ransomware attack, however, a statement was released saying that they have “reported recent abnormal situations” to the relevant DPAs and LEAs.
Acer’s Statement:
“Acer routinely monitors its IT systems, and most cyberattacks are well defensed. Companies like us are constantly under attack, and we have reported recent abnormal situations observed to the relevant law enforcement and data protection authorities in multiple countries.”
“We have been continuously enhancing our cybersecurity infrastructure to protect business continuity and our information integrity. We urge all companies and organizations to adhere to cyber security disciplines and best practices and be vigilant to any network activity abnormalities.” – Acer.
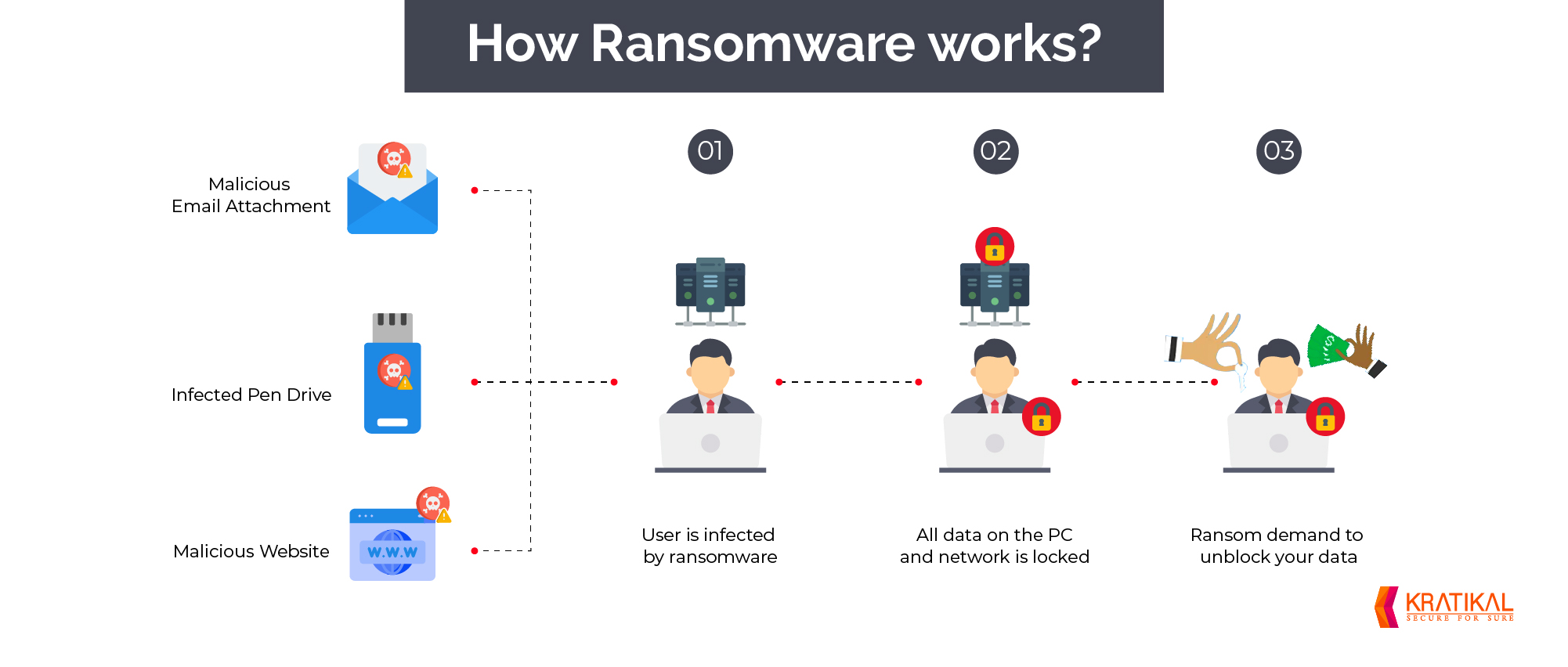
How Ransomware Works?
Wondering how ransomware attacks work exactly? There are several attack vectors cyber criminals can use to run a ransomware campaign. One of the most frequently used vectors is phishing.
Cyber criminals send out phishing emails with malicious attachments, which provide them with access to the victim’s device when downloaded or opened. Sometimes these malicious attachments come with built-in social engineering tools that trick the victim into allowing administrative access.
The outcomes can vary once the victim has downloaded the malicious attachment, but by far the most common consequence is that some or all of the victim’s files get encrypted. These files cannot be decrypted without the access key known only by the attackers. Consequently, the victim often ends up paying the ransom to get back access to the valuable files.
Mitigating the Risk of Ransomware Attacks
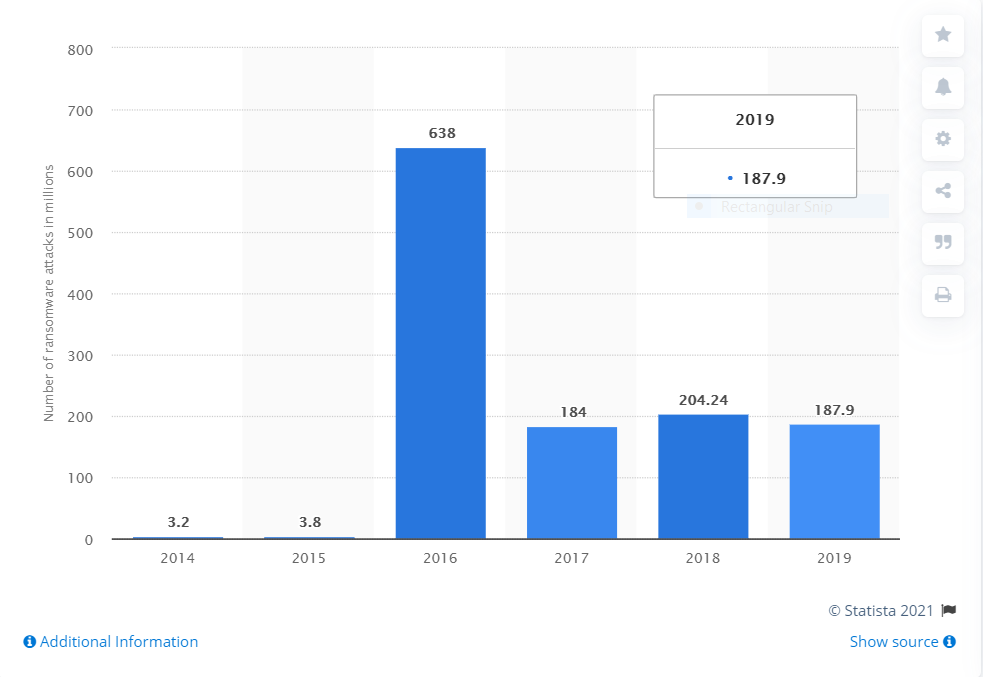
At this point, irrespective of the company size, no business is safe from the threat of ransomware. According to Statista, the number of ransomware attacks annually has never gone below 100 million since 2016.
Cyber criminals are getting greedier. As long as they can get money by holding some of your files hostage, you are a potential target. There is nothing stopping them from attacking you again even if you have already paid a ransom one before. Therefore, implementing the right cyber security measures to protect your organization against the threat is the smartest move.
So, what are the cyber security measures that cyber security experts should implement to defend their respective organizations?
Listed below are the 5 most common but effective ways to combat ransomware attacks:
- Instruct your employees to avoid installing any software or application from unknown sources or giving it administrative privileges before making sure it’s safe.
- Make sure every system and software is upgraded with the latest updates and security patches.
- Conduct VAPT periodically to identify the loopholes in your organization’s IT infrastructure and fix them on priority.
- Educate your employees about the threat of ransomware by providing them with the best cyber security awareness training with a tool like ThreatCop.
- Implement firewalls to stop malicious content from entering your network.
I’ll explain the preventive measures in further detail in my next blog. So stay tuned! Meanwhile, why don’t you share your own thoughts on ransomware attacks and the ways to avoid them in the comments section below.
Turn Your Employees Into A Cyber Threat Shield
Make your employees proactive against prevailing cyber attacks with ThreatCop!

