
Remember how we grew up learning fishing and farming as a source of earning money? Least did we know that this source of earning could be replicated as phishing and pharming cyber theft one day! The ever-evolving technology is not only offering efficient work resources but is also creating a path for cyber thieves to misuse it.
Today, cyber thieves are honing their cybertheft skills to beat the latest technology and innovative security systems to create havoc in the cyber world. Both phishing and pharming, the two major types of cyber thefts are being infamously used to trick users into providing their personal information. Cybercriminals use both of these tactics to obtain the sensitive information of users, however, both of these tactics work with different methods. Proceed further to find out how.
Table of Content
Definition of Phishing
A phishing attack is basically social engineering and identity theft that generally targets users with the aim to con them into revealing their personal and confidential information. In this technique, hackers send spoofed emails in the name of a legitimate source to victims and trick them into clicking on a malicious link or attachment to acquire their personal information.
In many instances, these phishing scams use software or security vulnerabilities to install malicious software in the targeted user’s device. In any case, the human factor remains the key element in the successful phishing attempts of these cyber crooks.
Phishing attacks are not limited to email phishing as phishers use SMS (smishing) and voice messages (vishing) to trick victims into providing their information by impersonating a legitimate source. As a result, these phishing attacks have become so convincing that they have accounted for 90% of data breached in 2019!
Definition of Pharming
Often known as “phishing without a lure”, pharming is a scamming practice of installing malicious code on a computer system or server to misdirect targeted users to fraudulent websites without its knowledge. These fraudulent websites are the look-alike of the legitimate ones to trick and misguide the victim.
While the method stays different, the goal of stealing personal information such as login credentials, financial information, personal details, etc. remains the same. A user can fall victim to pharming even on clicking on an authentic link if the website’s domain name system (DNS) has been hijacked by a hacker.
Just like a phishing attack, the pharming attack is equally dangerous for users online because, in this social engineering scam, the chances of recognizing any lurking danger are very low. It is a hidden threat because a user will never know if the website is hijacked or not before handing over the personal information on request.
What is the Difference Between Phishing and Pharming?
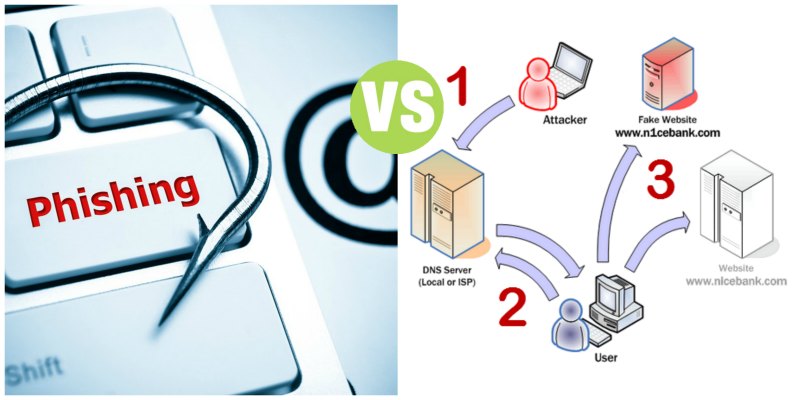
To understand the difference between phishing and pharming, it is important to understand the vector Domain Name System (DNS). In order to carry out pharming scams, hackers misuse DNS as the main weapon vector. While phishing attempts are carried out by using spoofed websites, appearing to have come from legitimate entities, pharming relies on the DNS server level.
Unlike phishing, pharming doesn’t rely on bait like fake links to trick users. Instead, it compromises the DNS server and redirects users to a simulated website even if the user has inputted the correct web address. For instance, if a hacker launches a successful DNS cache poisoning attack, it will alter the fundamental web traffic flow to the targeted website.
While phishing includes other techniques like smishing, vishing, fax phishing (phaxing), etc., pharming includes techniques like DNS spoofing, DNS hijacking, DNS cache poisoning, and all the DNS altering scams. Both data thefts are nothing but evolving online robbery that can lead any organization to devastating consequences.
Comparatively, pharming is more insidious than phishing because hackers manipulate the DNS level and make it difficult for users to identify. Phishing on the other hand tops the list of the art of social engineering by luring victims effortlessly into submitting their sensitive information on the misdirected phished website.
How to Prevent Phishing and Pharming?
Both phishing and pharming are serious cyber threats to any organization today. Regardless of their differences, these cyber scams lead to the same consequence: loss of confidential data for malicious use. In order to secure your organization from these cyber attacks, follow these effective guidelines as cybersecurity measures:
- Lookout for HTTPS in URLs
DNS spoofing doesn’t generally work on HTTPS websites. Even if the hacker manages to spoof a legitimate website and redirect a server under its control, it will not be of any use.
- Check for Suspicious-looking Emails
Phishing emails more than often consists of grammatical errors and suspicious-looking content. Also, the source of the email address in most cases is unknown, so it is always better to cross-check any unfamiliar or unexpected email.

- Cybersecurity Awareness Training
We can’t ignore the fact that employees are the most vulnerable link in the chain of cybersecurity. In order to strengthen this link, it is important to provide employees with proper security awareness training to guide them to identify the potential cyber risks.
- Brand Monitoring
Always keep track of how your brand is being represented online. Anti-phishing and fraud monitoring tools help in identifying if there is any online copyright infringement activity going on against your organization’s website or application.
- Avoid Clicking on Links
Emails are the successful carriers of malicious attachments like links, document files, images, etc. Try to avoid clicking suspicious or unexpected email attachments as they redirect users to fraud web pages and request personal information. Make sure to verify such emails on an incident response tool so as to avoid becoming a target of any cyber attack.
- Email Authentication Protocols
Why pay for recovering damages of cyberattacks when you can easily invest in right cybersecurity solutions and that too in comparatively less cost? Secure your email domain from unauthorized access with email authentication protocols such as DMARC, dynamic SPF, and dynamic DKIM.
Phishing and pharming cyber thefts are becoming more complex day by day! How endangering are these potential threats to an organization?
Comment your answer below and let us know what you think.
Thank you for giving your valuable time to read this blog, hope you had a good read!
Turn Your Employees Into A Cyber Threat Shield!
Make your employees proactive against prevailing cyber attacks with ThreatCop!

