
Watering Hole Attack: The Attack Vector Used In Targeting Florida Water Utilities!
Do you know that no less than 1,000 end-user computers visited the site infected by the attackers during the 58-day window! But what are these attacks and how do they affect an organization? Well, this blog sums it all!
Cyber criminals keep coming up with new ways to scam individuals and organizations globally out of their money and data. One of the popular attack vectors being adopted by the hackers these days is watering hole attacks. With cyber crimes rising every day, organizations around the world are striving to stay ahead of this growing threat. This requires knowledge of all the prevalent and emerging cyber attack vectors being used by the threat actors.
Table of Content
What is a Watering Hole Attack?
A watering hole attack is a cyber attack designed to target a specific group of users either by infecting the websites usually visited by the targeted users or by luring them to a malicious site. Also referred to as strategic website compromise attack, this attack vector aims to infect the systems of the targeted users to gain unauthorized access to their organization’s network.
Watering hole attacks are targeted attacks and may seem similar to spear phishing but trap more victims at once than spear phishing does. In these attacks, hackers create new sites or compromise legitimate applications and websites using difficult and zero-day exploits with no antivirus signatures, ensuring a high attack success rate. The most prominent highlight of watering hole attacks is that the victims may not even realize that they’ve been compromised until much later.
How Does a Watering Hole Attack Work?
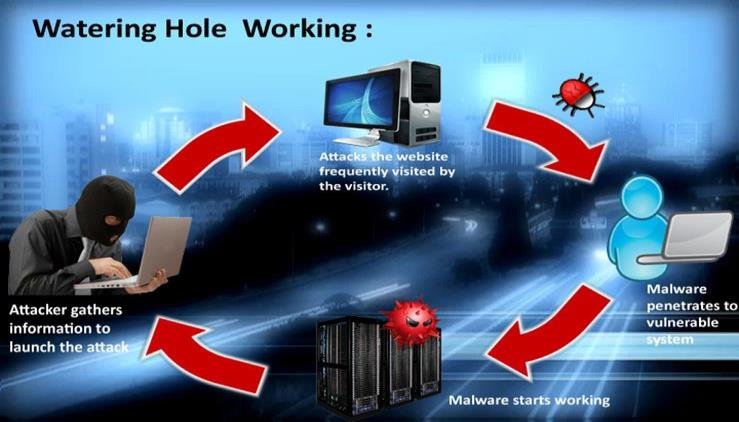
Launching a successful watering hole cyber attack requires proper planning and execution by threat actors. To protect yourselves and your organizations against such attacks, it is essential to know how they are carried out. So, here is how a watering hole attack works:
Step 1: The hackers profile the users they are targeting based on their industry, job title, organization, etc. This helps them in determining which type of websites and applications are often visited by the targeted users or the employees of the targeted organization.
Step 2: Then, the threat actors either create a new website or look for any vulnerabilities in the existing applications and websites to inject malicious code, which redirects the users to a malicious site.
Step 3: Doing this, they manage to infect the system of the target with malware.
Step 4: The hackers can now exploit the malware infection to initiate malicious activities. They often collect usernames and passwords for launching credential-stuffing attacks on targeted applications, sites and organizations.
Step 5: Once a user’s system is compromised, the threat actors can perform lateral movements within the network to ultimately breach the entire organization.
How to Prevent These Attacks?
Data theft, financial losses and damage to company reputation are some of the most common consequences of watering hole attacks. With the frequency and severity of these attacks growing rapidly, it is essential to take every precaution you can to make sure your organization stays safe.
So, here are some of the measures you can take to prevent watering hole cyber attacks from taking place.
1. Conduct Periodic VAPT: Vulnerability Assessment and Penetration Testing (VAPT) can help you make sure that your security controls provide satisfactory protection against application and browser-based threats like watering hole attacks.
2. Keep the Systems Updated: Keep all your hardware and software up-to-date with the latest security updates and patches. Failing to do so can create weaknesses in your security infrastructure and lead to cyber attacks.
3. Be Wary of Third-party Traffic: All third-party traffic, no matter where it comes from, should be treated as untrusted until and unless it has been otherwise verified.
4. Enable MFA: Implement Multi-Factor Authentication (MFA) across all the applicable endpoints of your organization’s networks. This will reduce the impact of watering hole attacks in case the attackers manage to steal the user credentials of your employees.
5. Establish a Cyber Resilient Work Environment: Educate your employees about watering hole attacks to make them more vigilant. Providing your staff with proper cyber security awareness training is the best way of creating a cyber resilient work environment. You can make use of tools like ThreatCop to make the training sessions more effective and engaging.
So, keep these tips in mind and make cyber security a priority to shield your organization against the vicious attacks by cyber criminals.
Do you have any more suggestions for preventing watering hole attacks? Let us know in the comments section below!
Get your hands on the latest DMARC report!
Check out the latest trends in Email Security

