
While the world was still reeling from the fallout of “WannaCry”, another ransomware attack took the world by surprise. The ransomware has been spotted predominantly in many organizations in Ukraine but according to security researchers, it has also seen in other European countries. Global firms like Maersk have been affected. This fresh strain of malicious code dubbed “Petya” was first spotted encrypting computers in Ukraine with Windows SMBv1 vulnerability.
Petya is a malicious piece of ransomware and works very in a different way from any other malware. Being different from other traditional ransomware, Petya does not encrypt files on your system but simply reboots potential victim’s computer systems and encrypts the master file table (MFT) in hard drives and thus restricting the right to use to the full system by seizing all information on the physical disk.
In simple terms, Petya encrypts the MFT and overwrites the MBR with a custom bootloader. In contrast with the conventional ransomware which encrypts the file system, Petya renders the entire disk unusable.
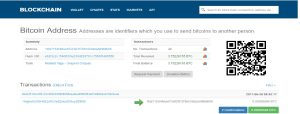
This is the real time transaction happening in the “Petya ransomware”. Till now 42 times victims have paid to the ransomware attack. For more details you can click here:
How Petya ransomware spreads?
Petya ransomware is hitting systems by means of the same leaked NSA vulnerabilities used by the WannaCry attack. Early examination of some of the ransomware illustration established that the malware creators used the EternalBlue exploits. But it’s important to mention that the flaw used in these attacks is still unclear as no phishing emails have yet emerged. The one thing that is clear is the latest ransomware is scattering swiftly, even on patched Windows systems.
This ransomware has majorly inflicted healthcare, financial and retail sectors.
Post successful exploitation of any Windows PC, the malware downloads the main executable binary through the Command and Control Server and performs encryption of the disk. It then reboots the systems at noon (logic bomb) and shows the ransom note.
What to do if infected?
Are you thinking of paying a hacker to get your files back? If so then drop your idea as it’s advised not to pay the ransom.You need to have proper awareness of what to do once infected. The brains behind this attack usually communicated with their victims using the email id wowsmith123456@posteo.net
Once it came to their notice, the German email provider suspended the email address
So the attackers might not even get your mercy plea. So to secure yourself, you need to do beforehand preparation for cybersecurity in your organization.
Preventive steps to take if you are affected by the ransomware:
The Petya ransomware infects computers and then waits for an average 1 hour before rebooting the machine. To avoid the calamity, you can switch off the computer to prevent the files from being encrypted and try to save the files from the machine. Disconnect your system from the internet, reconfigure the hard drive, and reinstall your files from a backup. Some major countermeasures include:
- Block source E-mail address–wowsmith123456@posteo.net
- Disable SMBv1
- Update Anti-Virus definitions
- Back up your files regularly and keep your anti-virus software up to date.
- Filter connections to unknown domains
- Maintain strong firewall rules and Access Control Lists (ACLs)


I really like what you guys tend to be up too. This type of clever work and reporting! Keep up the excellent works guys I’ve added you guys to my blogroll.|
Thank you, Herbert! It’s a pleasure to know that you find our blogs interesting.