
Table of Content
What is a Secure Code Review?
Secure Code Review is the process to check the code in the development phase so that there are no vulnerabilities left in the code. It involves manual and automatic testing of the code, which helps to review the loophole in the code that can later affect the organization. It is a process to identify and patch coding errors in the development phase before they turn into a high-level security risk. Reviewing security codes helps an organization to minimize the overall maintenance and development cost by enhancing the effectiveness of the code lines and eliminating any kind of early-stage risks.

Major Focus Pointers for Code Review
Injection:
The injection is a flaw that allows the application to accept the inputs to enter shell commands, enter the database, or operating system, which makes the application vulnerable for injection attacks.
Memory Flaws:
The flaws like Meltdown and Spectre are caused due to inconsistent and vulnerable code, which ends up compromising the information and data present in the primary memory.
Sensitive Data Exposure:
When due to the vulnerability in the program code, an attacker can gain sensitive information like the credit card details, private data, passwords, etc is known as the sensitive data exposure.
Cross-Site Scripting:
The cross-site scripting is similar to the injection attacks. In this, the malicious scripts are embedded in such a way that the user’s PC trusts the malicious site by using the cookies as a legit site. This involves the browser side scripting and compromising the user.

Principle of Secure Code Review
The principle of secure code review or the peer code review is that after this process, there should be no short-comings, security loose ends, code structure loopholes, and inconsistency in the code. It is done for the quality assurance of the code and thus, the code is read and rewritten mitigating all the possible vulnerabilities.
Purpose of Secure Code Review
Secure Code Review is an important step during the development process these days. It allows the code to be free from any kind of risk. It is important for the application to have consistency. It should be free from any security vulnerabilities and data discrepancies. The code should have a proper structure and ways to manage the data.
How is the Code Reviewed?
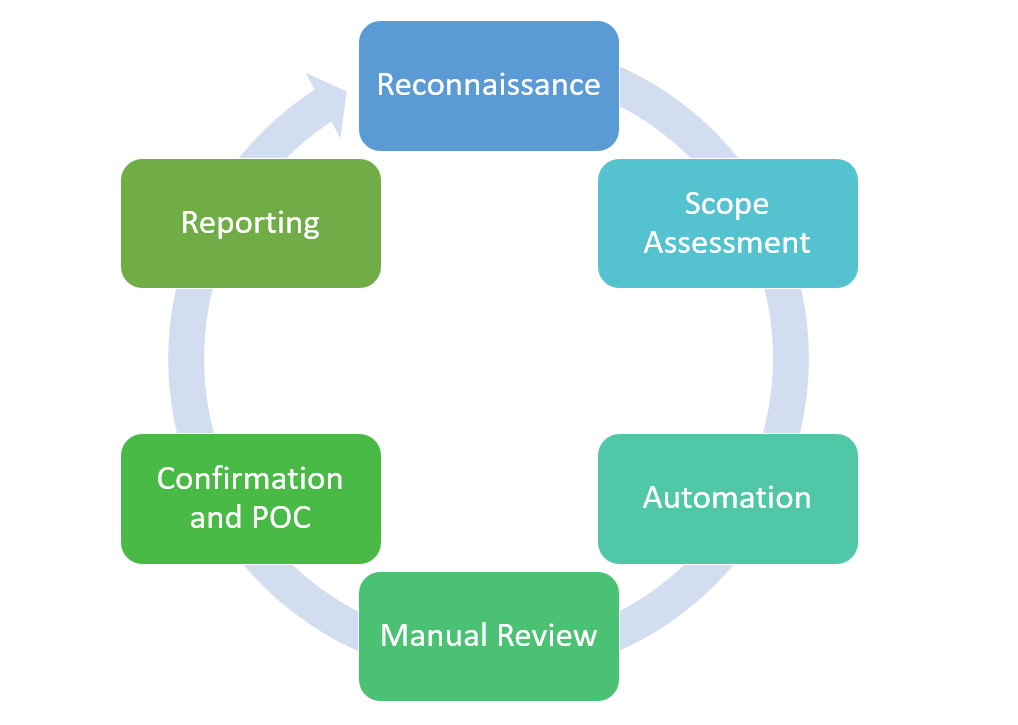
There are 6 steps to secure code review: –
Reconnaissance:
The reconnaissance is the process where we see the code and try to figure out the basic threats and risks in it.
Scope Assessment:
Threats and risks are categories and scope is decided for the same. This scope helps us to follow a path in the next processes. This is known as the scope assessment.
Automation:
Based on the scope the code is checked using various tools. These tools automate the process following the checklist. Thus, this makes the process automated.
Manual Review:
After using the tools in the automation step. The code is manually checked to find out the issues if any. The left vulnerabilities are removed manually.
Confirmation and POC:
After the code is reviewed by an automated and manual process, it is sent further for the confirmation and proof of concept (POC). Thus, this step checks that the code is good to go and can be sent for compilation.
Reporting:
Once all the processes are done and are confirmed, the report is made for all the steps taken. This report contains the vulnerabilities that were there in the code and suggestions to mitigate them. This final report covers all the information on the secure code review process.
Attacks Summary Due to Lack of Secure Code Review in 2019-2020
- 68% of a data breach of web applications
- 27% of personal data of the US stolen from websites
- 31% of credential data stolen from companies
- 82% of vulnerabilities were in application code
- 54% of cross-site scripting attacks were done because of loopholes in application codes
- 29% of injection attacks took place due to no secure code review
Do You Know
Who Is The Weakest Link In The
Cyber Security Chain?
You will be shocked but…it is your EMPLOYEES!
Make your employees proactive against prevailing cyber attacks with ThreatCop!

